Securing Node.js applications is crucial to prevent various security vulnerabilities and protect your application and its users. Here are some security best practices for Node.js applications:
1. Keep Dependencies Updated:
- Regularly update your project’s dependencies, including Node.js itself, npm packages, and other libraries. Vulnerabilities are often discovered and fixed in newer versions.
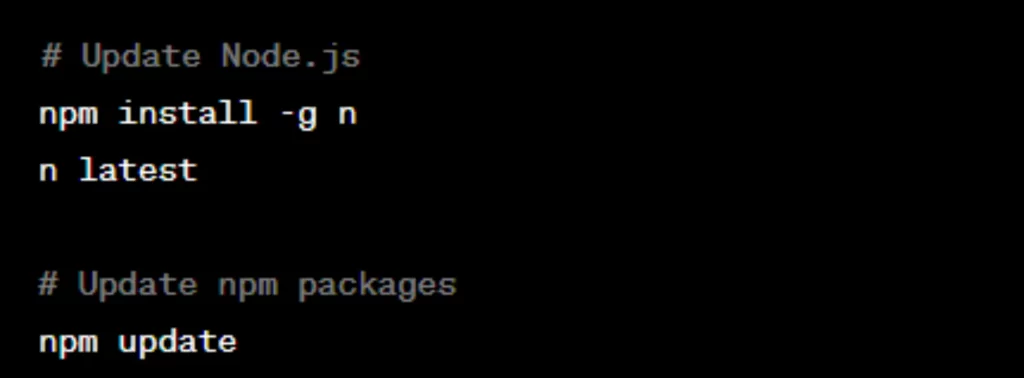
2. Use LTS (Long Term Support) Versions:
- Prefer using LTS versions of Node.js for stability and long-term support. LTS versions receive security updates for an extended period.
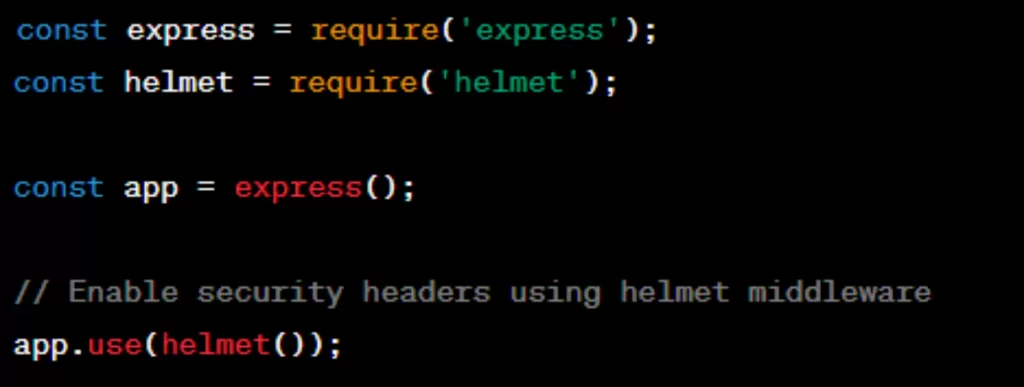
3. Enable Security Headers:
- Implement security headers in your application to mitigate common web vulnerabilities. For example, use headers like
Strict-Transport-Security,Content-Security-Policy, andX-Content-Type-Options.
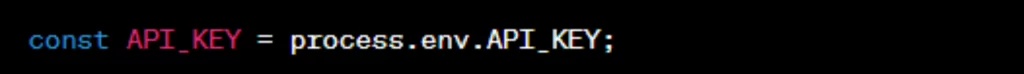
4. Handle Environment Variables Securely:
- Store sensitive information (such as API keys, database credentials) in environment variables and avoid hardcoding them in your code.
5. Use HTTPS:
- Always use HTTPS to encrypt data transmitted between clients and servers. Obtain and install SSL certificates to enable secure communication.
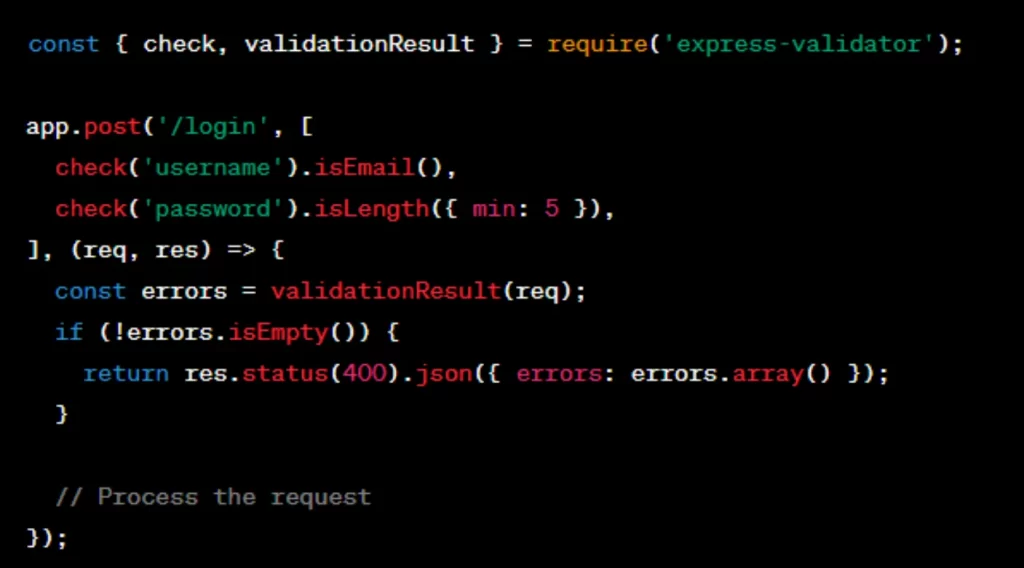
6. Validate User Input:
- Implement input validation and sanitize user input to prevent common vulnerabilities like SQL injection, Cross-Site Scripting (XSS), and Cross-Site Request Forgery (CSRF).
7. Use Parameterized Queries:
- When interacting with databases, use parameterized queries or prepared statements to prevent SQL injection attacks.
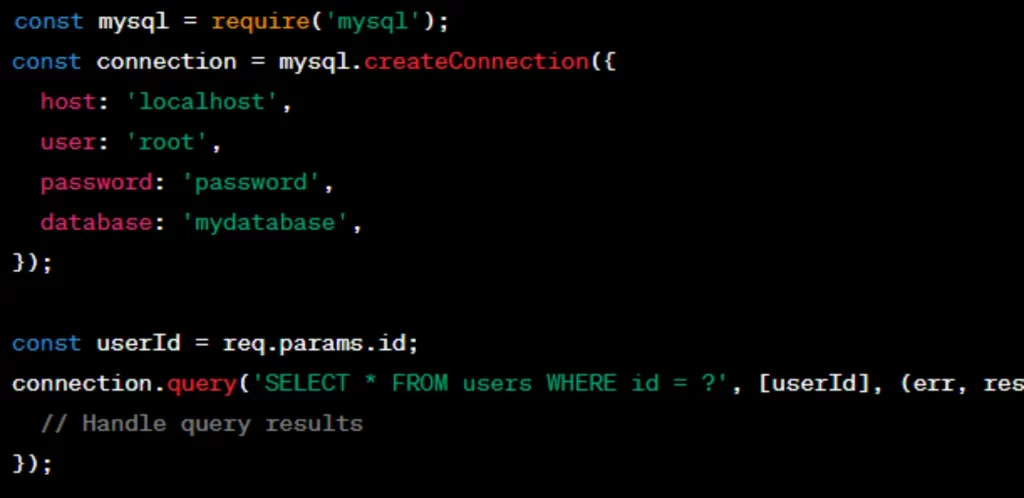
8. Implement Authentication and Authorization:
- Use secure authentication mechanisms like JWT (JSON Web Tokens) or OAuth. Implement proper authorization checks to ensure that users have the necessary permissions.
9. Protect Against Brute Force Attacks:
- Implement rate limiting and account lockout mechanisms to protect against brute force attacks on authentication systems.
10. Handle File Uploads Securely:
- When allowing file uploads, restrict allowed file types, validate file sizes, and store files in a secure location. Avoid serving files directly from user input.
11. Use Security Linting:
- Employ security linters, such as ESLint with security rules (e.g., eslint-plugin-security), to catch common security issues in your code.
12. Implement Cross-Origin Resource Sharing (CORS) Safely:
- Use CORS headers to control which domains can access your resources. Specify allowed origins, methods, and headers to prevent unauthorized cross-origin requests.
13. Monitor and Log Security Events:
- Implement logging for security events and monitor logs regularly. Set up alerts for suspicious activities.
14. Secure Session Management:
- Use secure session management practices. Enable secure, HTTP-only cookies, and consider using frameworks like Express Session with secure session stores.
15. Regular Security Audits:
- Conduct regular security audits and code reviews. Perform penetration testing to identify and fix potential vulnerabilities.
16. Educate Development Team:
- Ensure that your development team is educated about security best practices and stays informed about the latest security threats and patches.
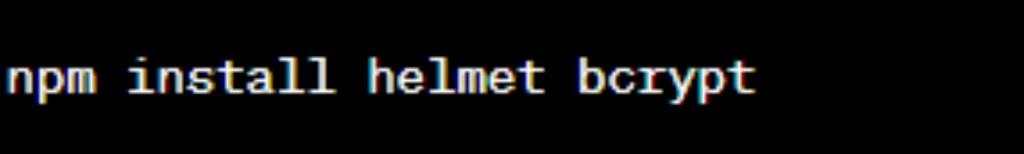
17. Use Security Libraries:
- Leverage security libraries and frameworks (e.g., Helmet, bcrypt) to handle common security concerns.
18. Security Headers:
- Implement security headers, such as Content Security Policy (CSP), to mitigate XSS attacks by controlling which resources a browser is allowed to load.
19. Dependency Scanning:
- Use tools like npm audit or third-party services to scan dependencies for known vulnerabilities.
20. Container Security:
- If using containers (e.g., Docker), ensure container security by regularly scanning images for vulnerabilities, limiting privileges, and following container security best practices.
By incorporating these security best practices into your Node.js application development lifecycle, you can significantly reduce the risk of security vulnerabilities and enhance the overall security posture of your application. Keep in mind that security is an ongoing process, and staying vigilant against emerging threats is essential.
